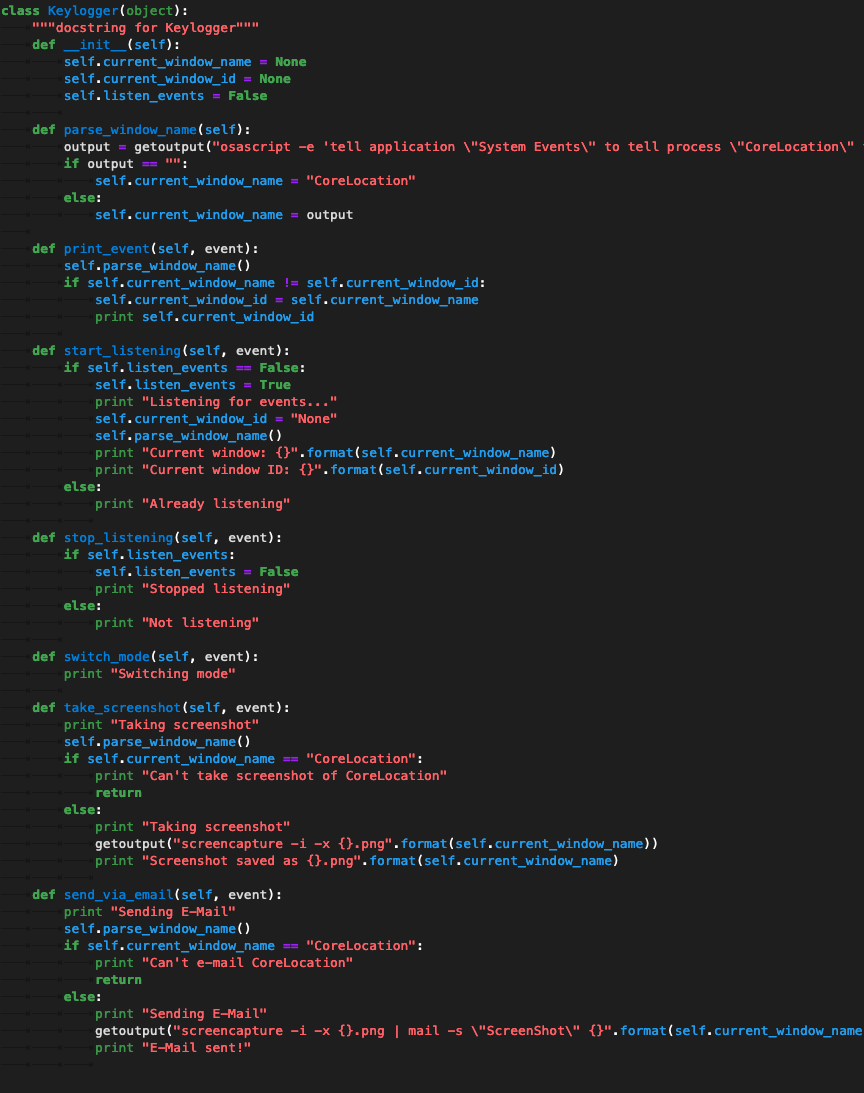
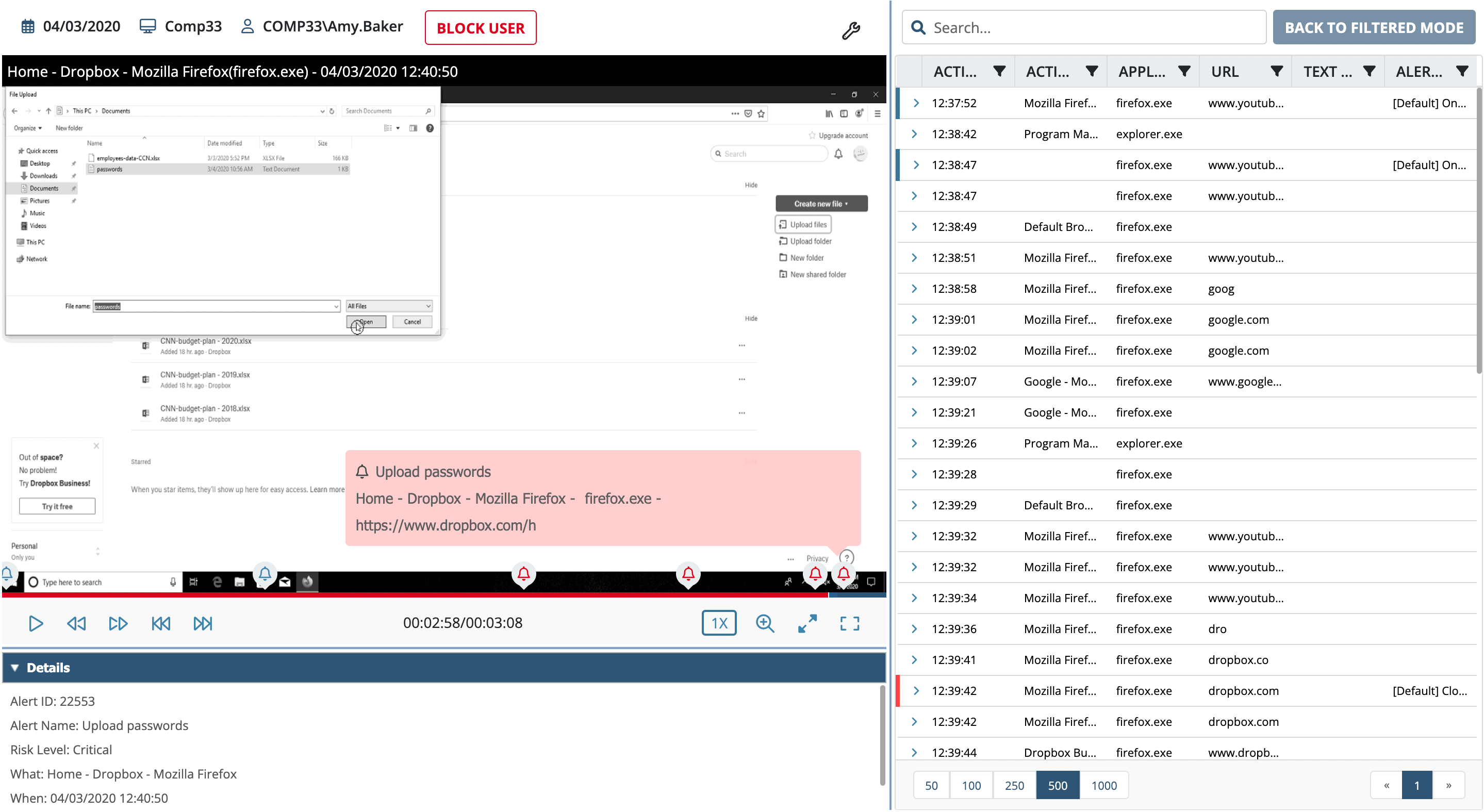
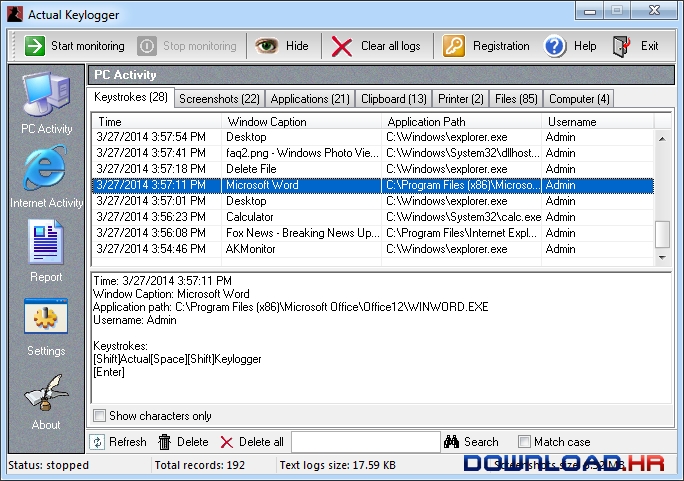
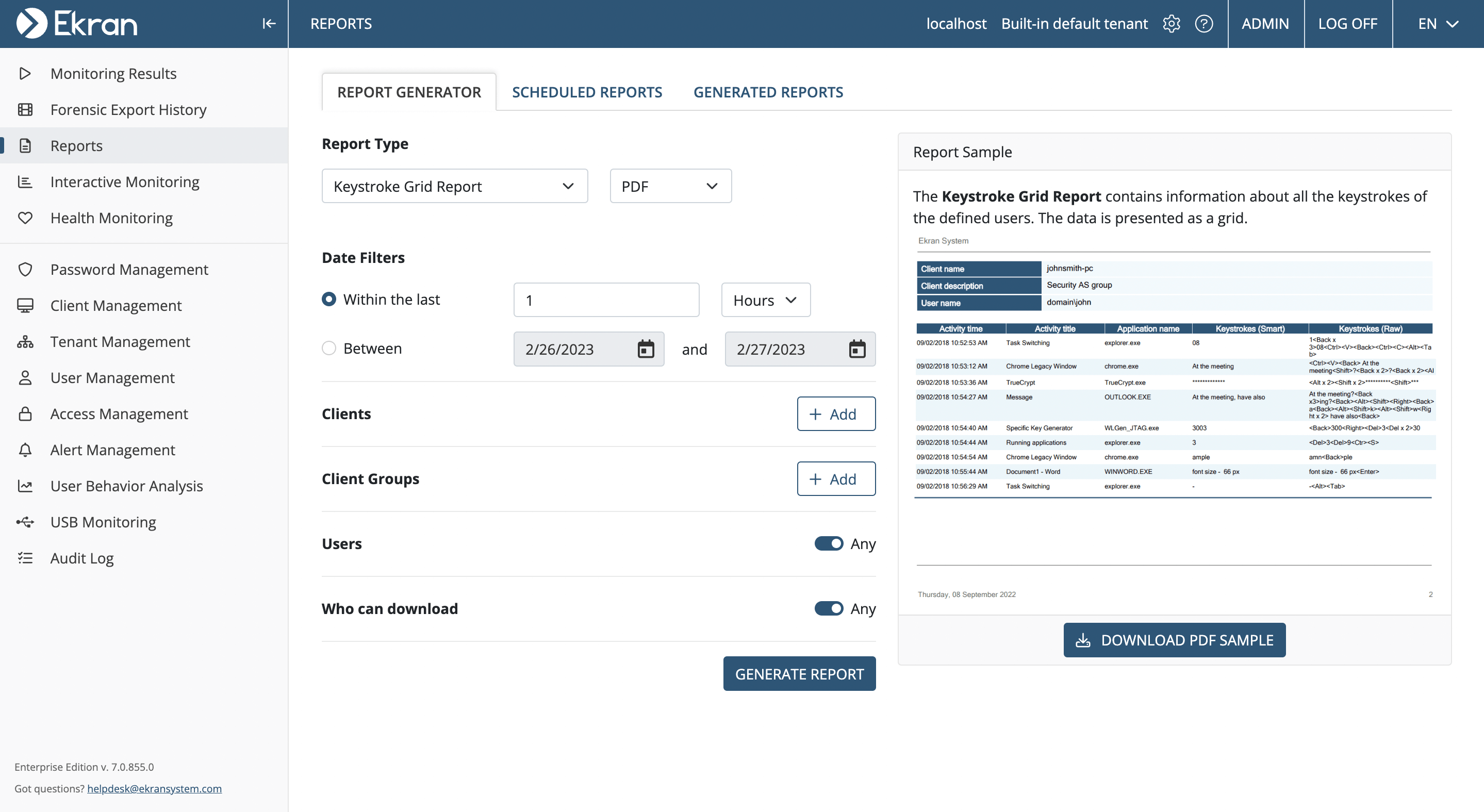
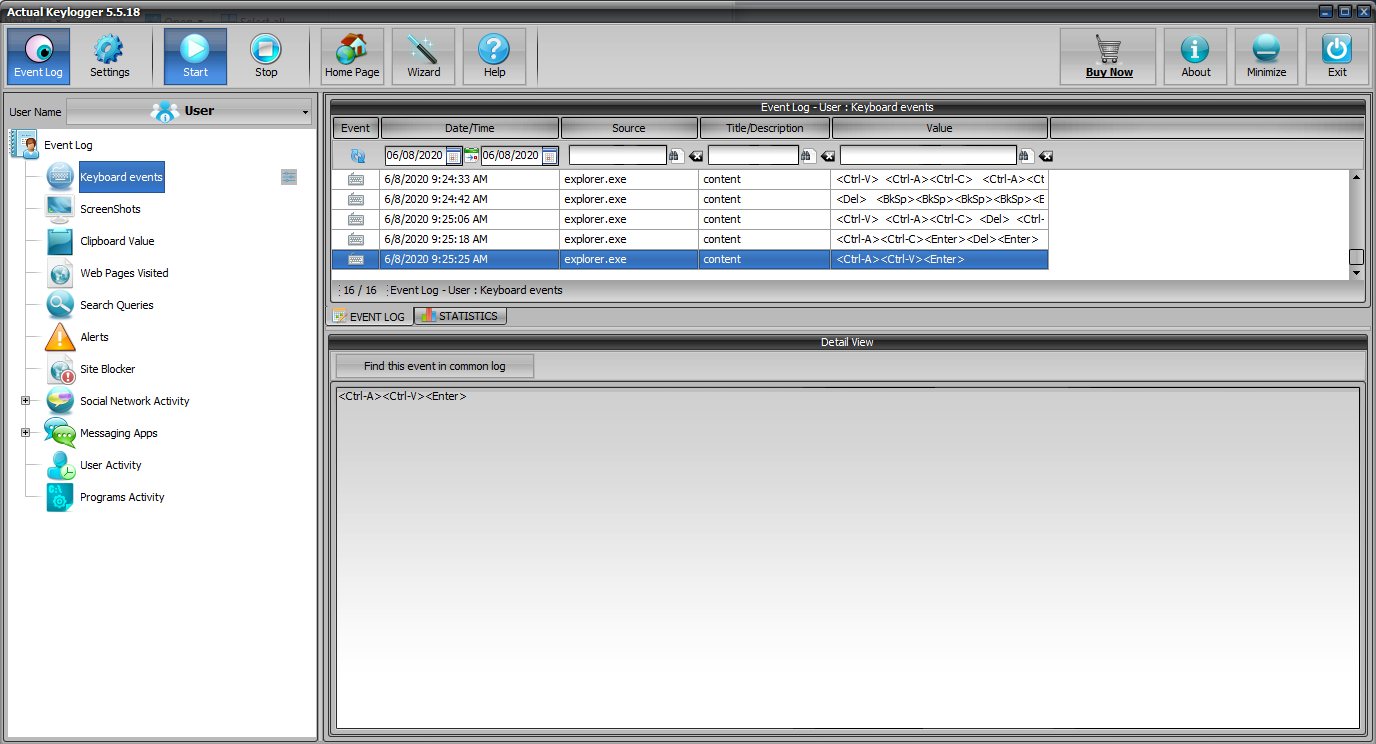
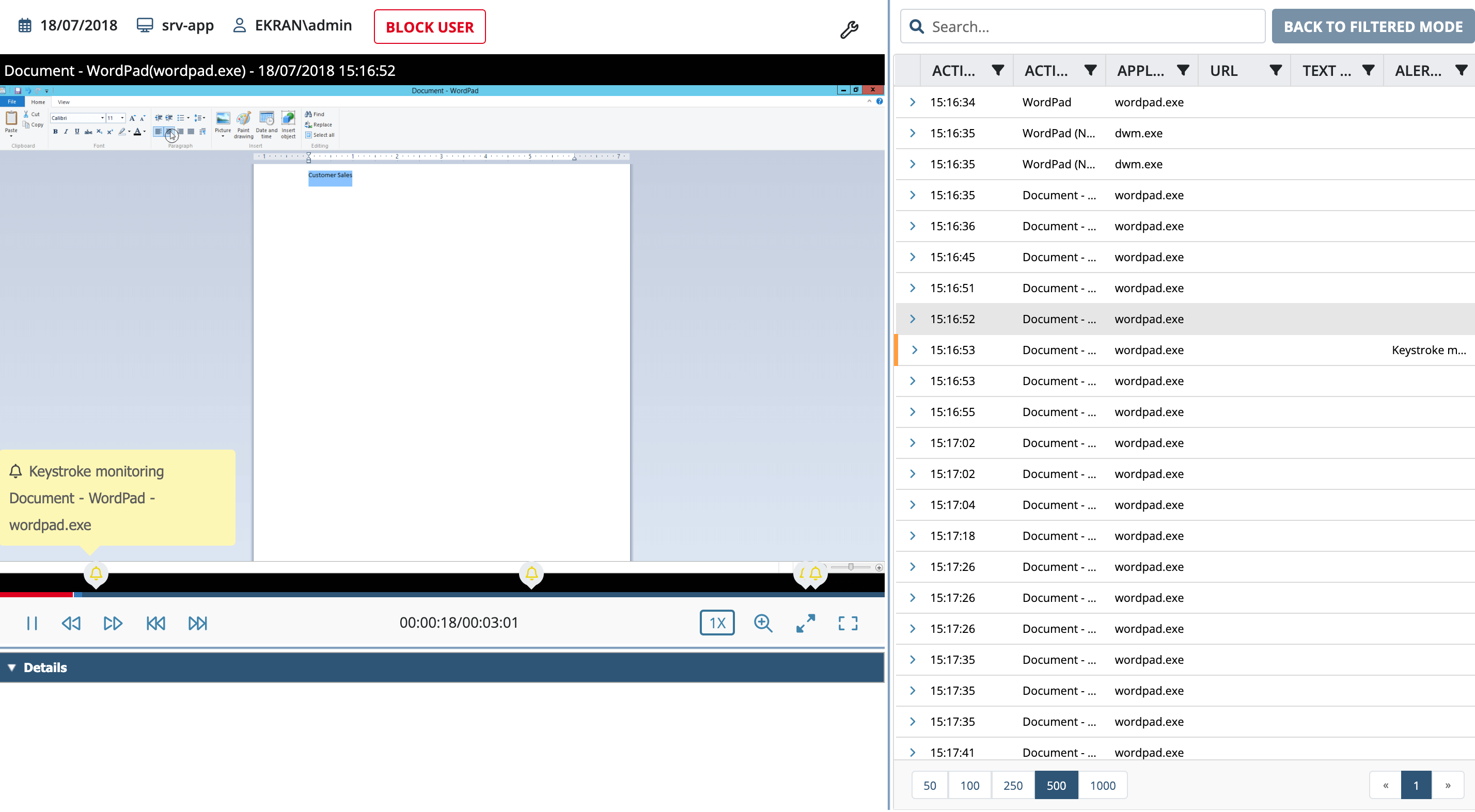
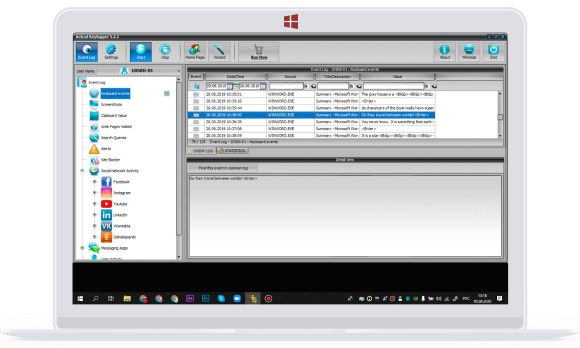
Keylogger Surveillance System - School of Science and Technology - Hong Kong Metropolitan University
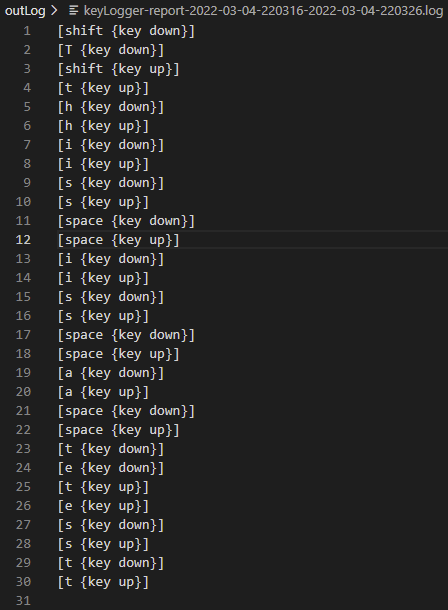
Keylogger Surveillance System - School of Science and Technology - Hong Kong Metropolitan University

Mathematics | Free Full-Text | CBFISKD: A Combinatorial-Based Fuzzy Inference System for Keylogger Detection

Under the Hood of SnakeKeylogger: Analyzing its Loader and its Tactics, Techniques, and Procedures | Splunk

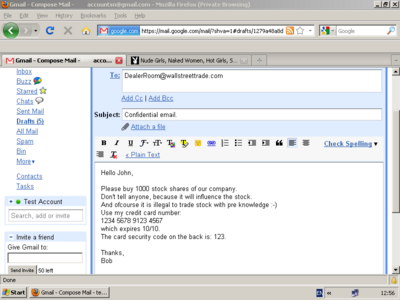
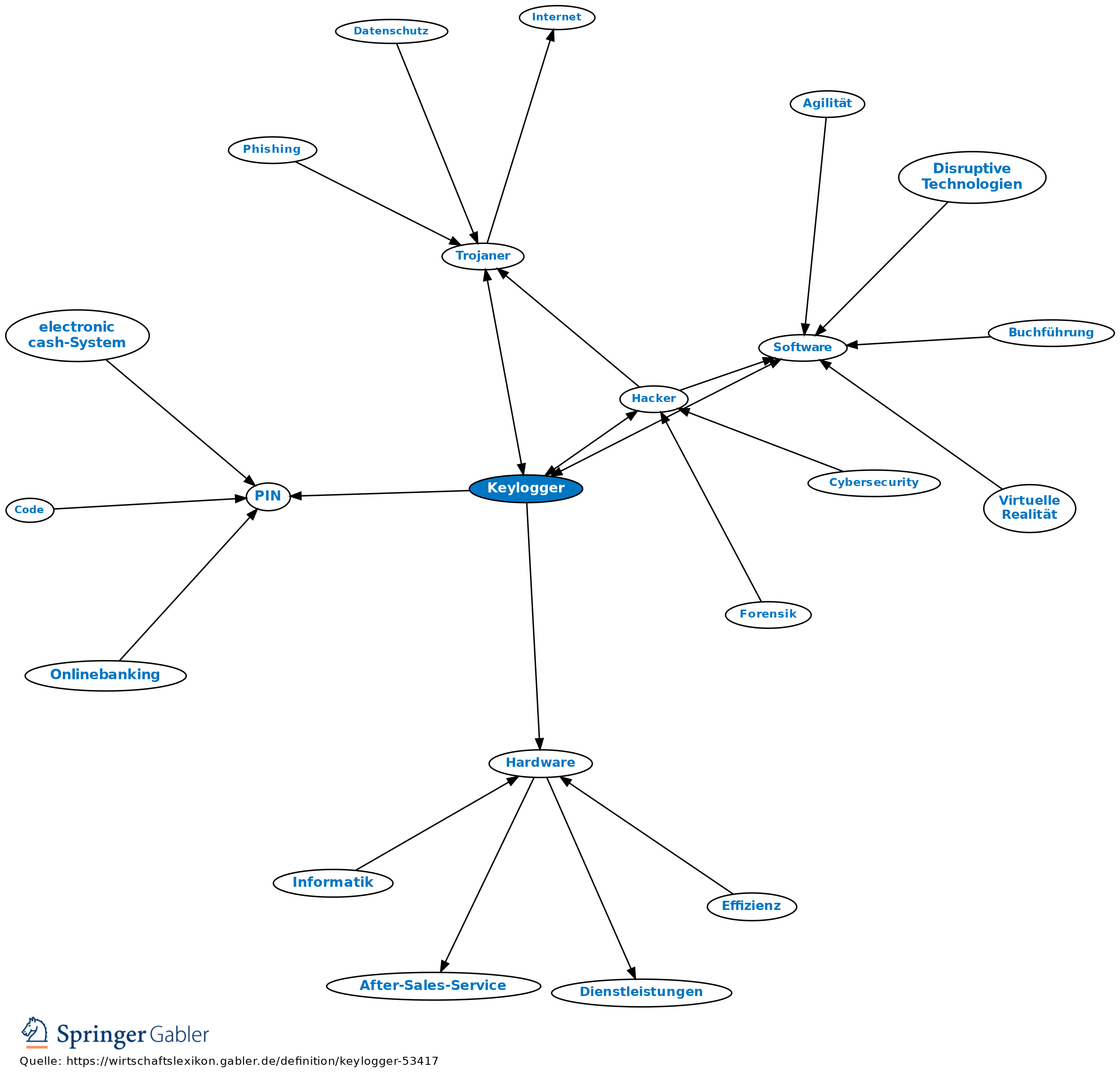
Die Geheimnisse der Keylogger entschlüsseln: Von der Eingabeaufzeichnung bis zum Cyberangriff - Hornetsecurity – Cloud Security Services for Businesses



:quality(90)/p7i.vogel.de/wcms/fb/ea/fbea70c7a47fbaec6cd6c8118d6c0aeb/0116168000.jpeg)