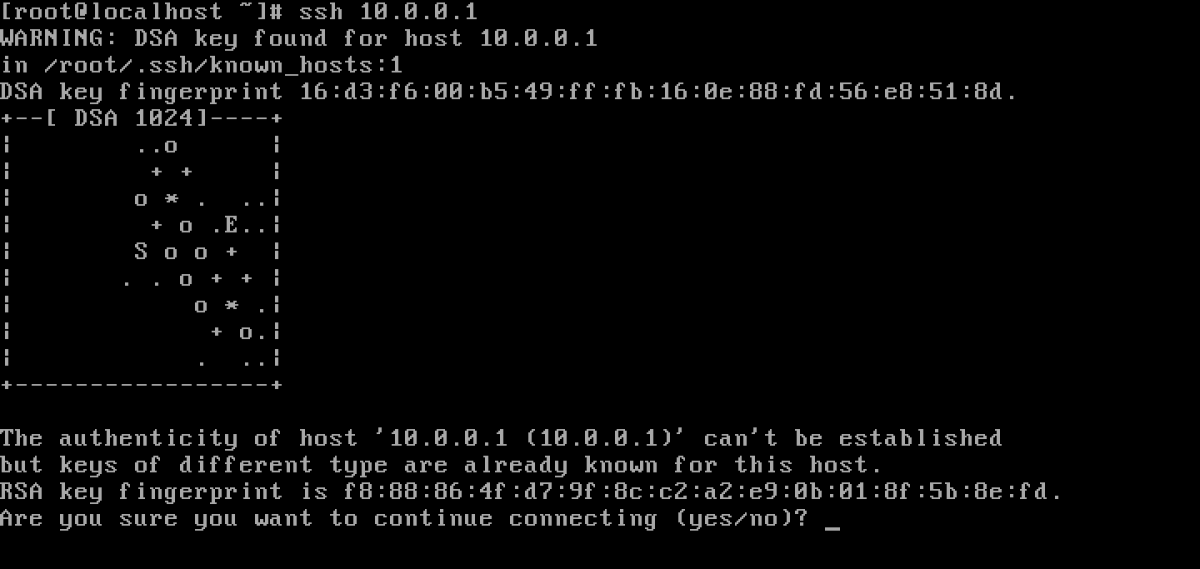
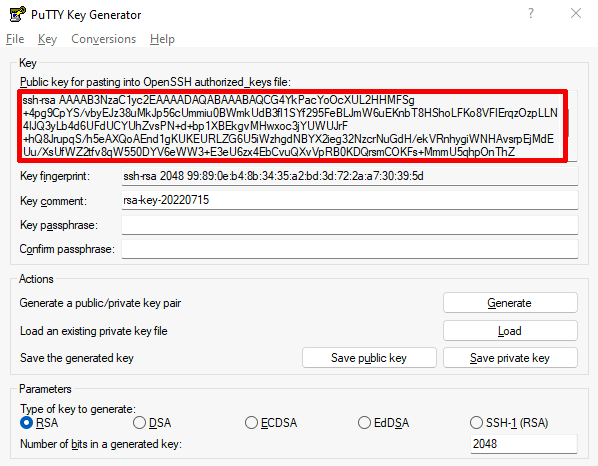
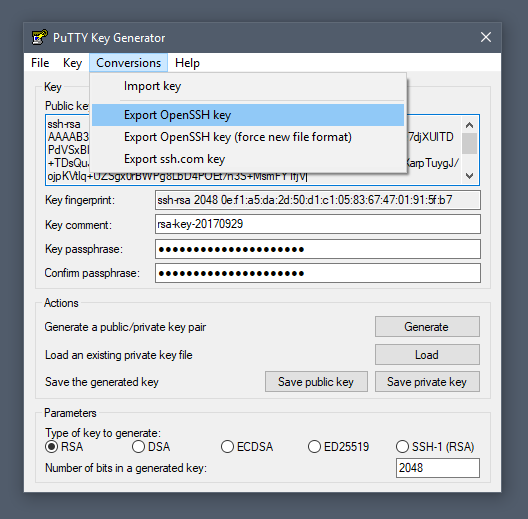
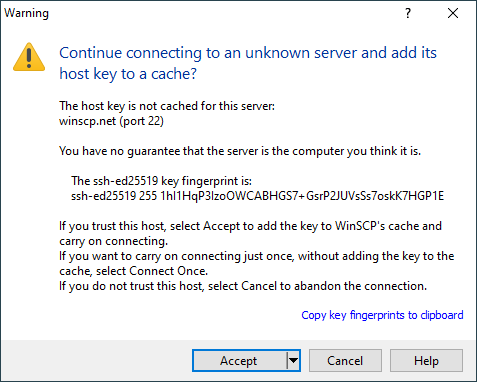
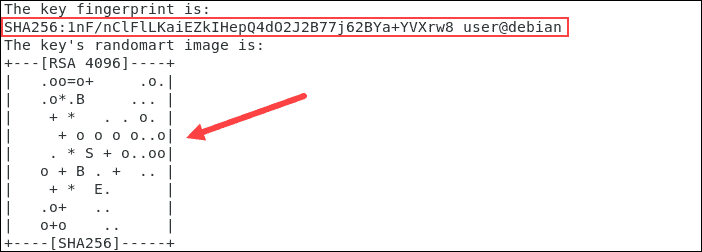
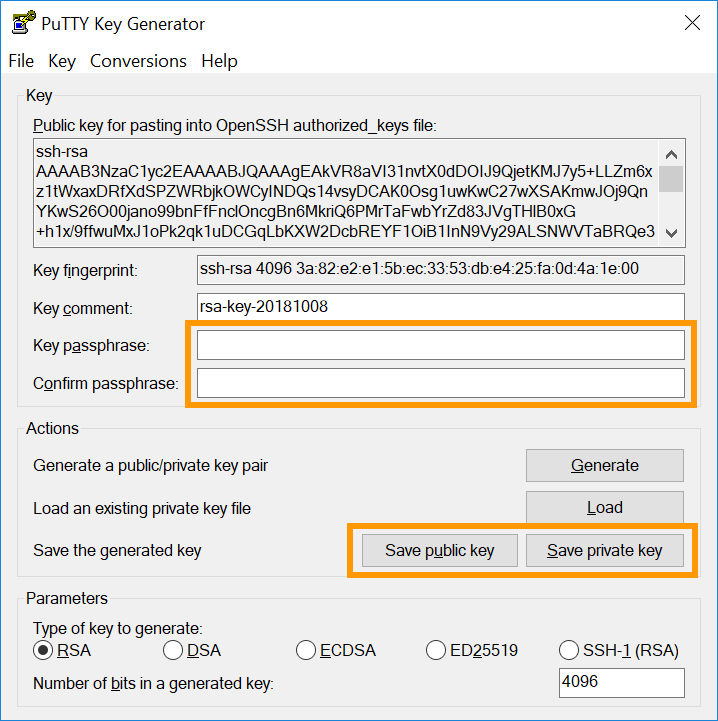
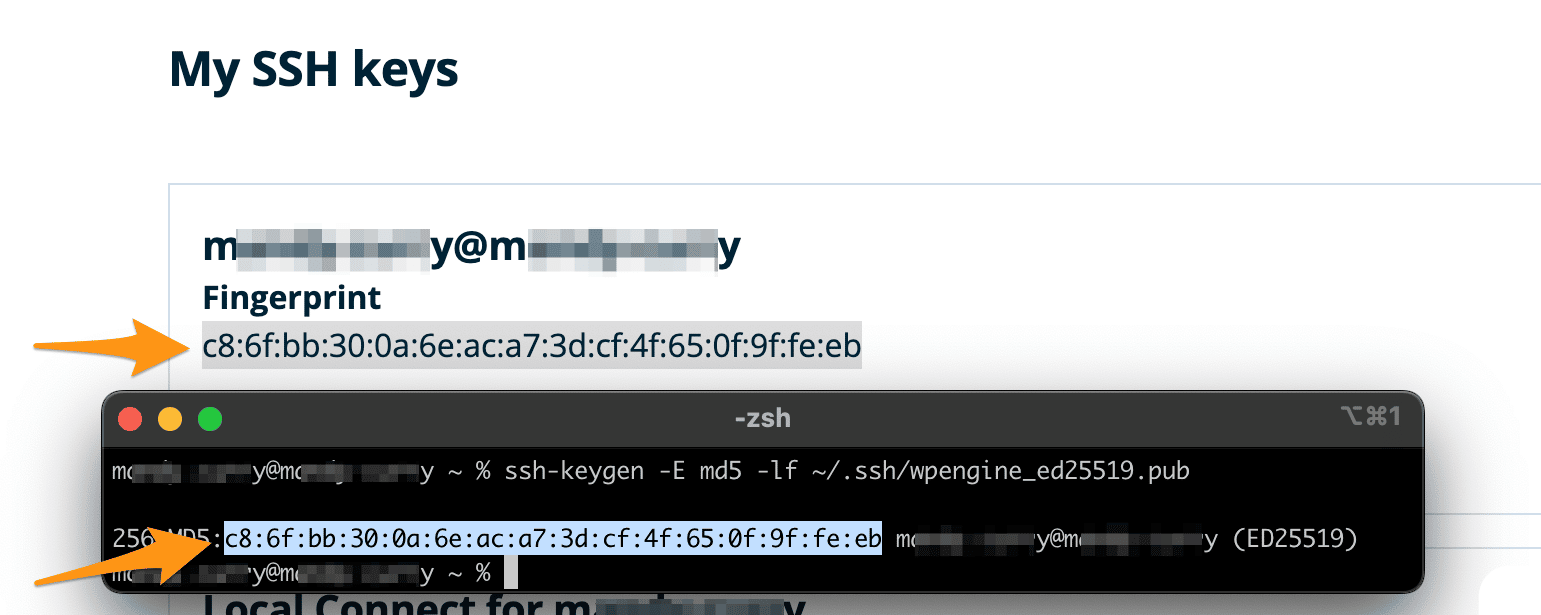
How can I confirm SSH fingerprint when connecting to a new Amazon EC2 instance using PuTTY? - Server Fault
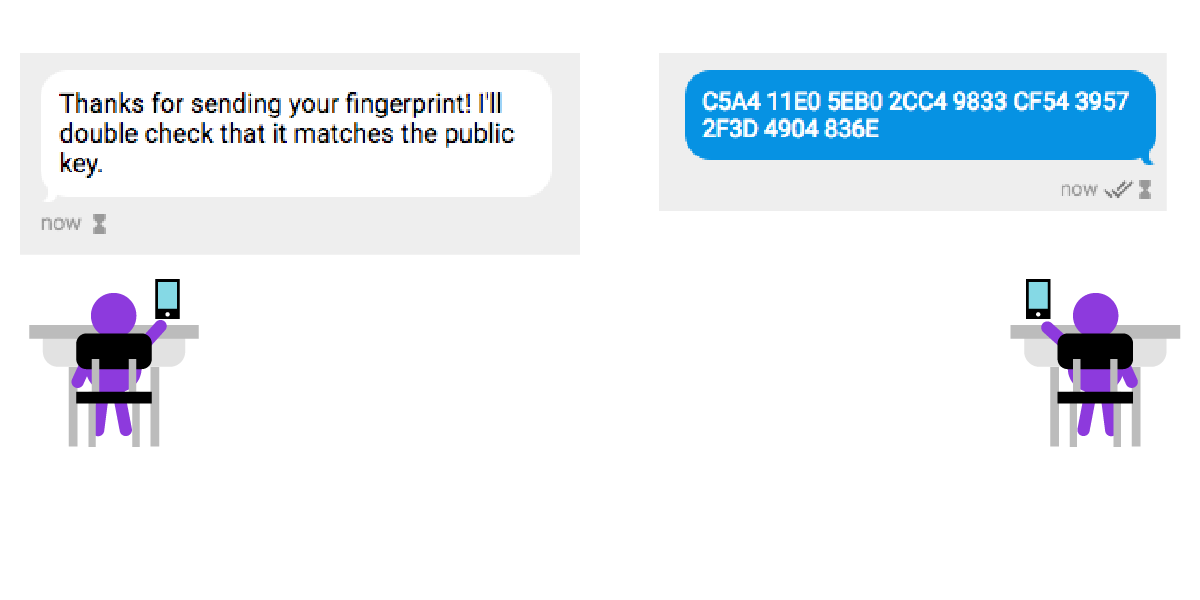
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense
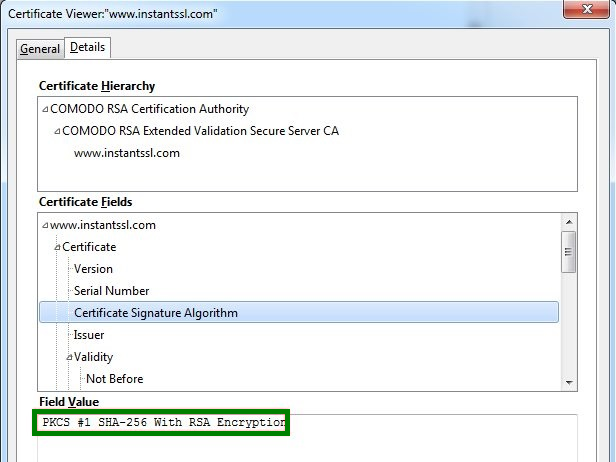
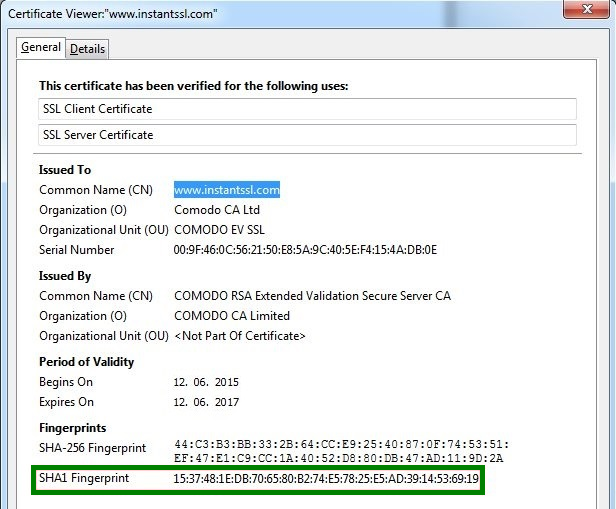
I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2? - SSL Certificates - Namecheap.com