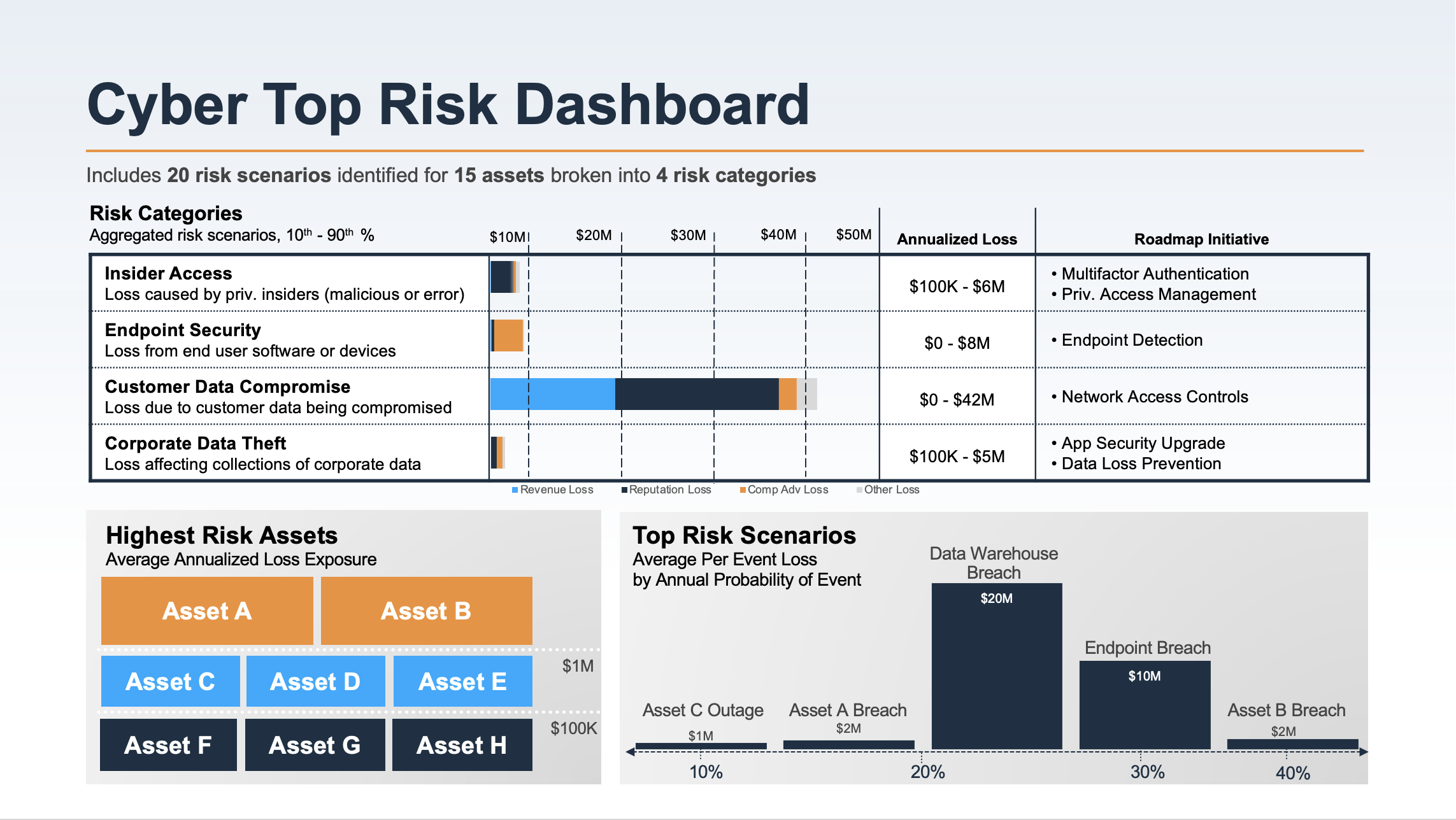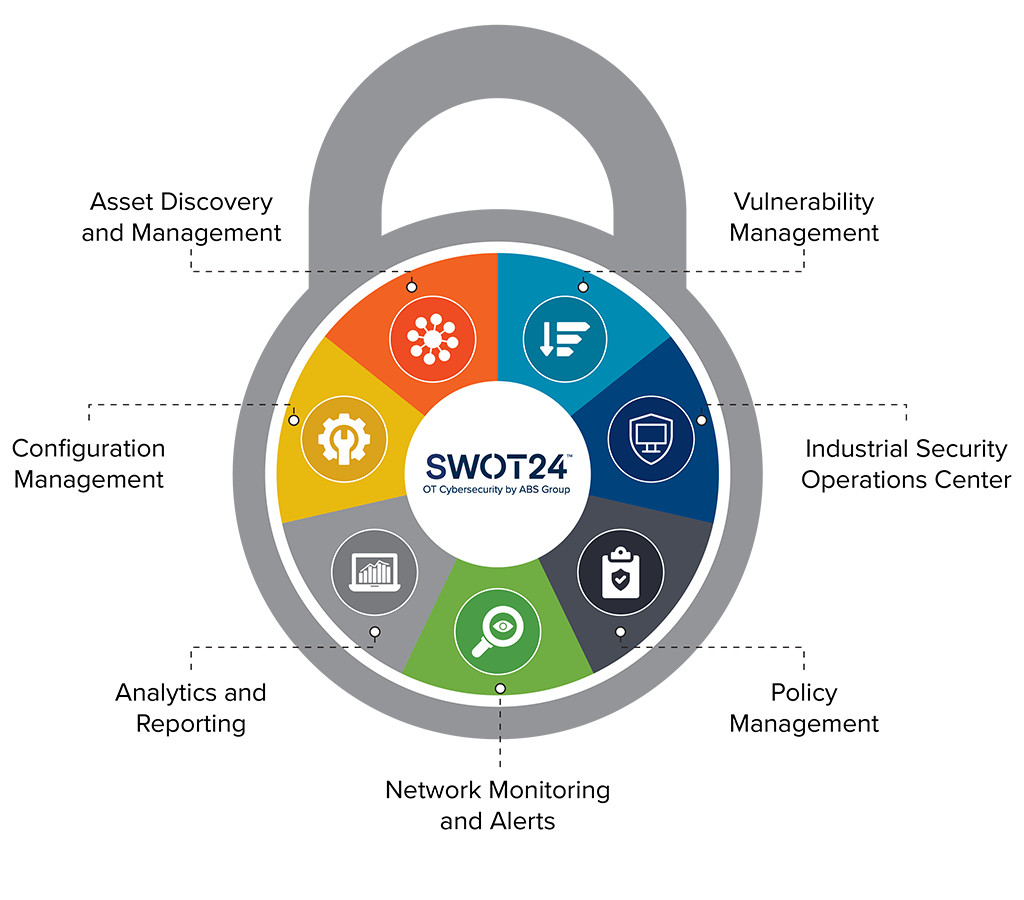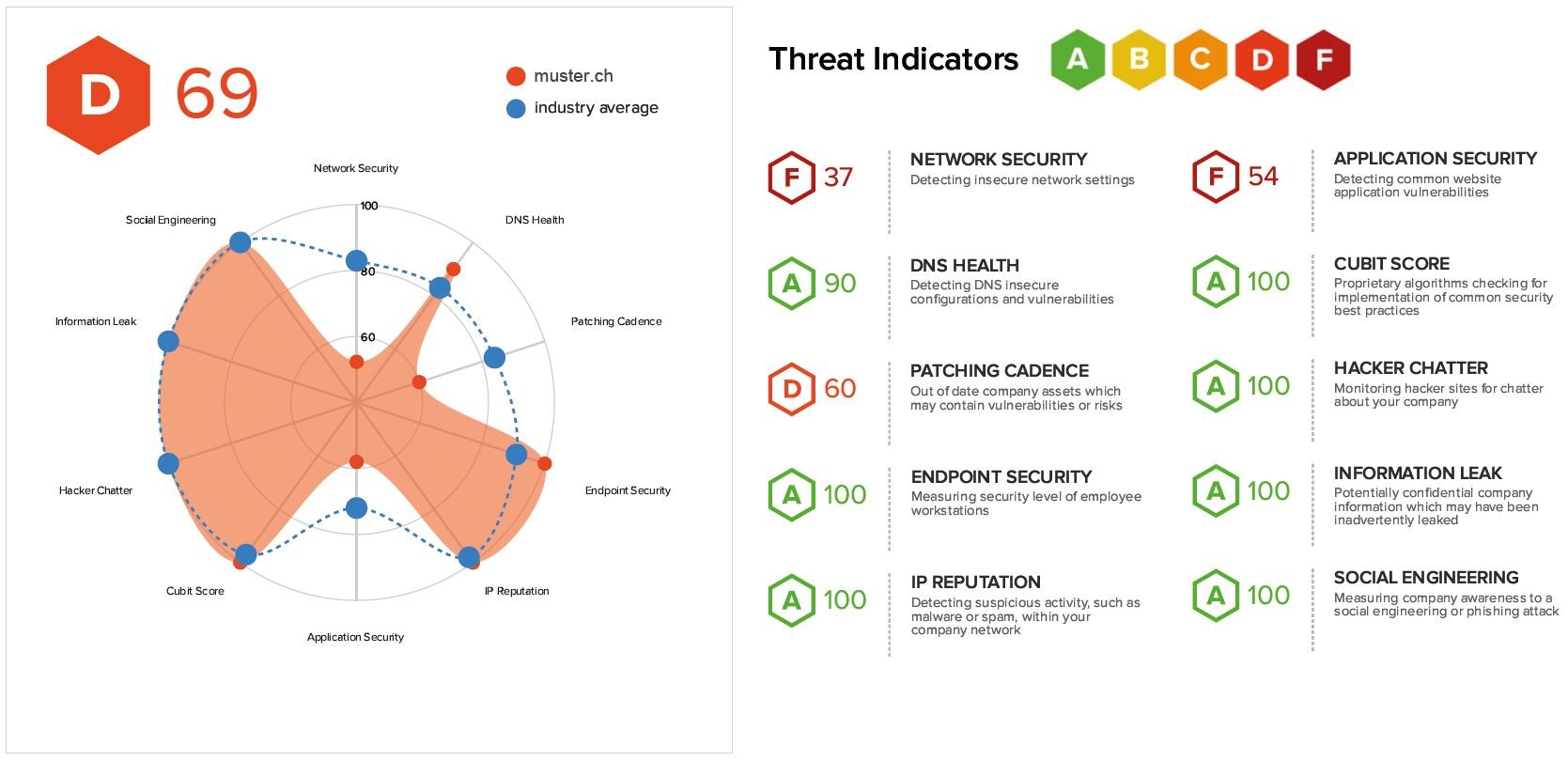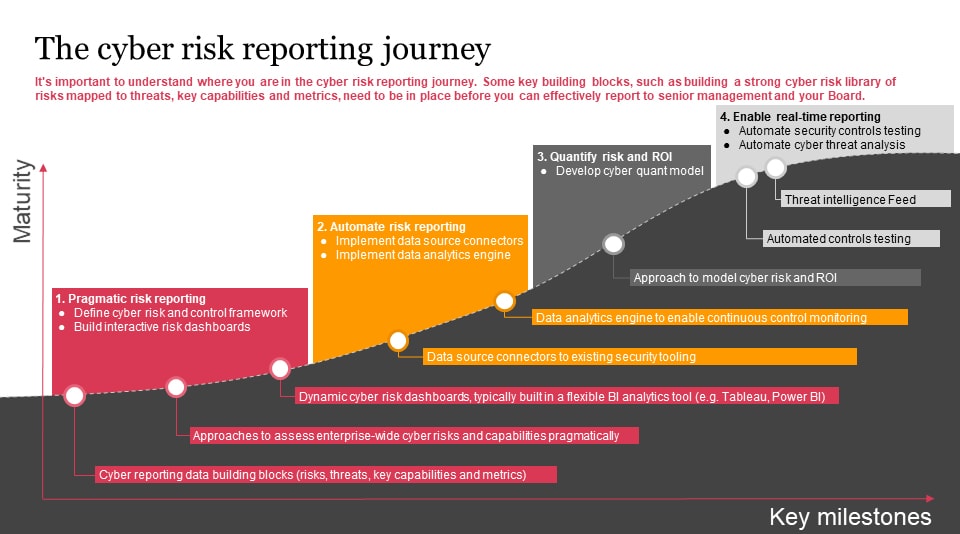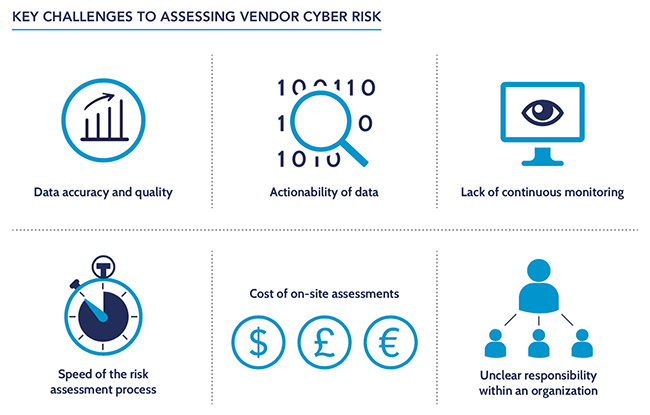
Current and emerging third-party cyber risk management approaches and challenges - Help Net Security
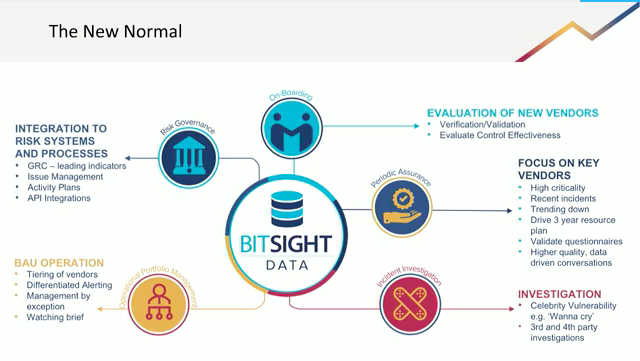
On-Demand: Cybersecurity Ratings Part 1: Continuous Cyber Risk Monitoring - Adapting to the New Normal | Bitsight
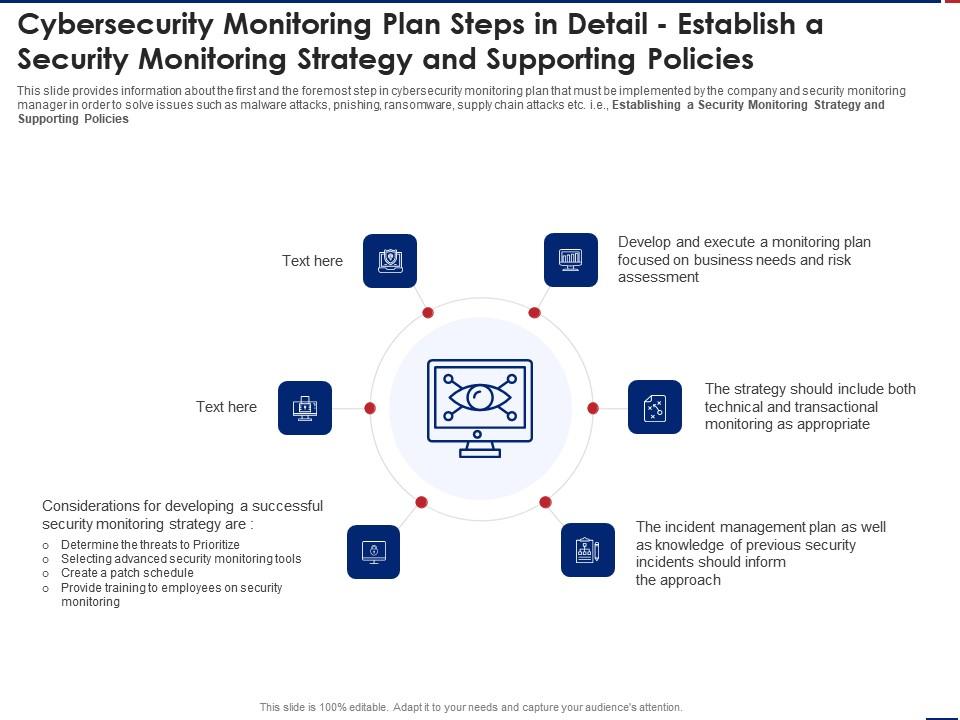
Effective Security Monitoring Plan Cybersecurity Monitoring Strategy Ppt Pictures | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Systemic cyber risk management for enterprise network. The asset owner... | Download Scientific Diagram