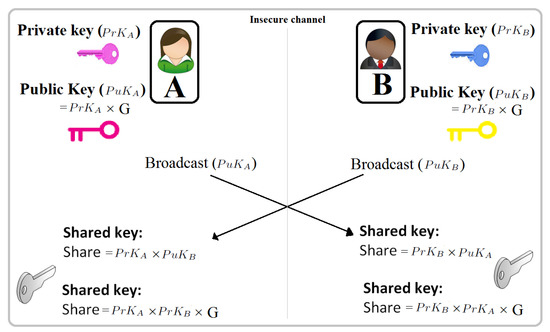
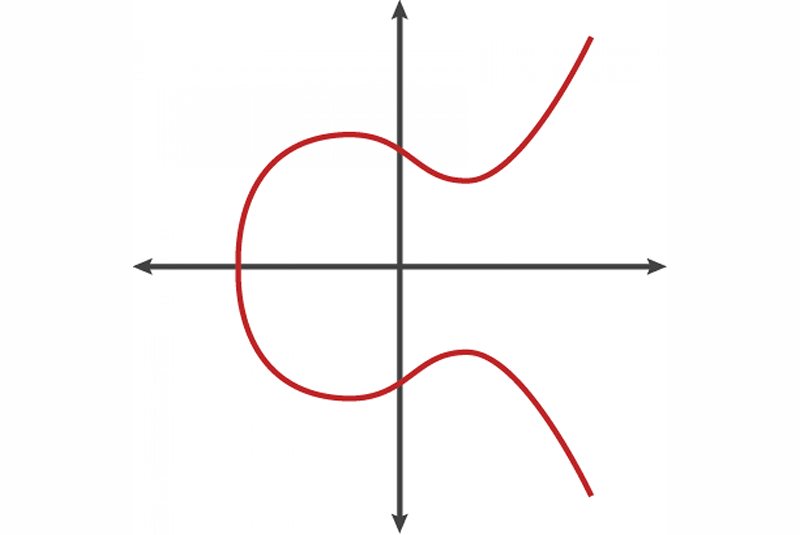
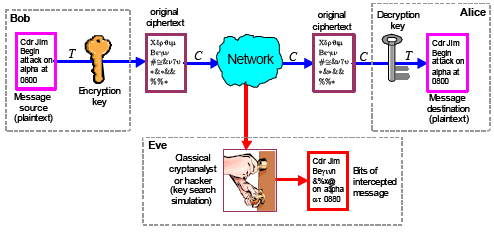
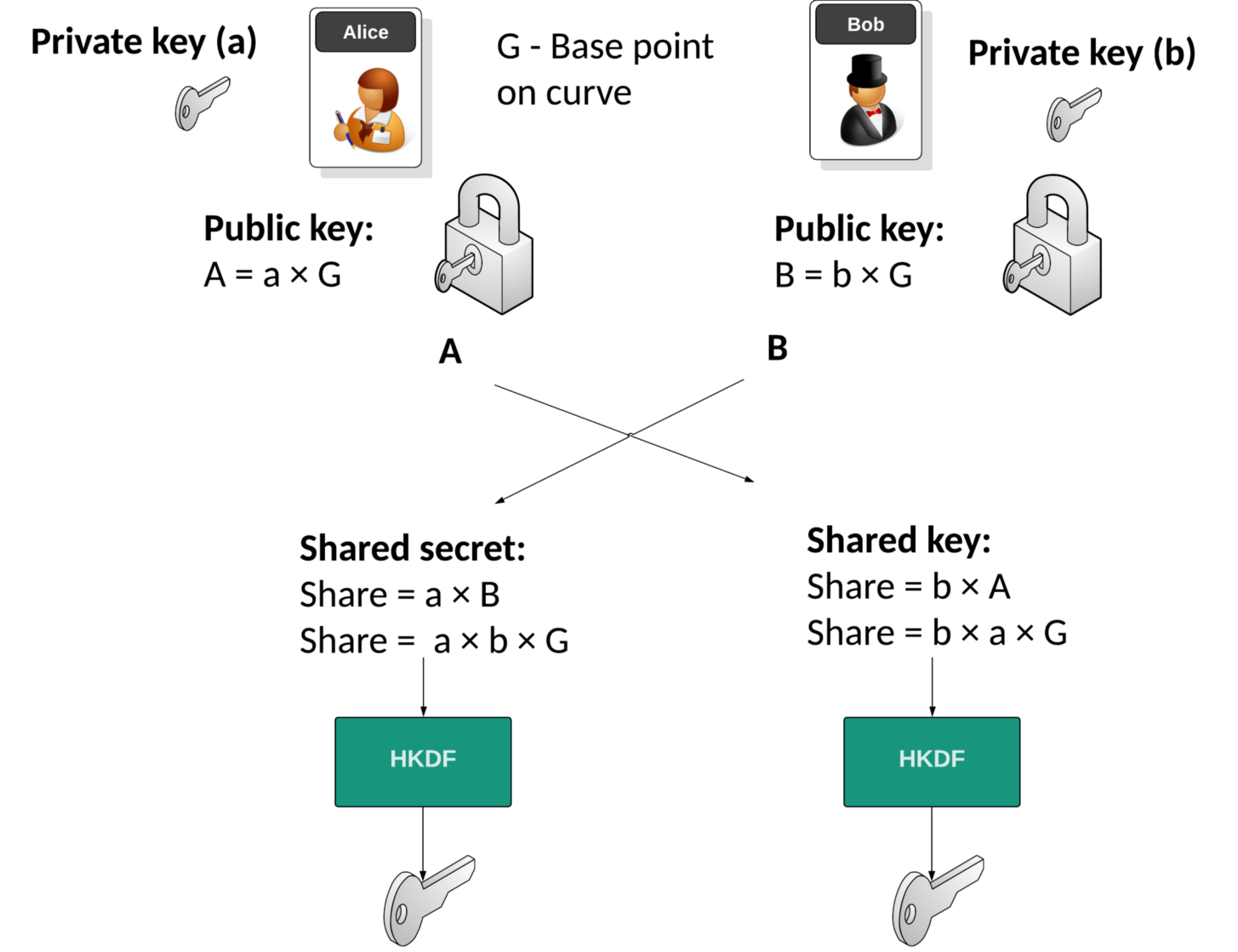
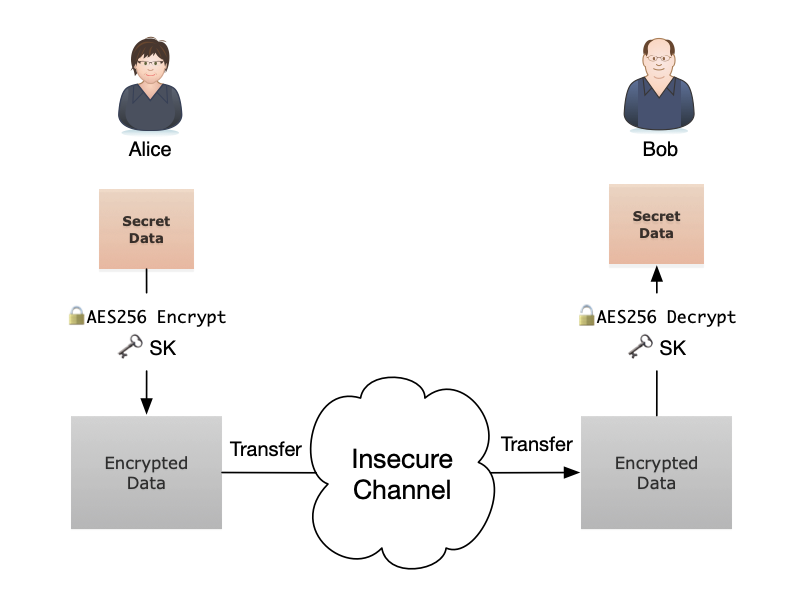
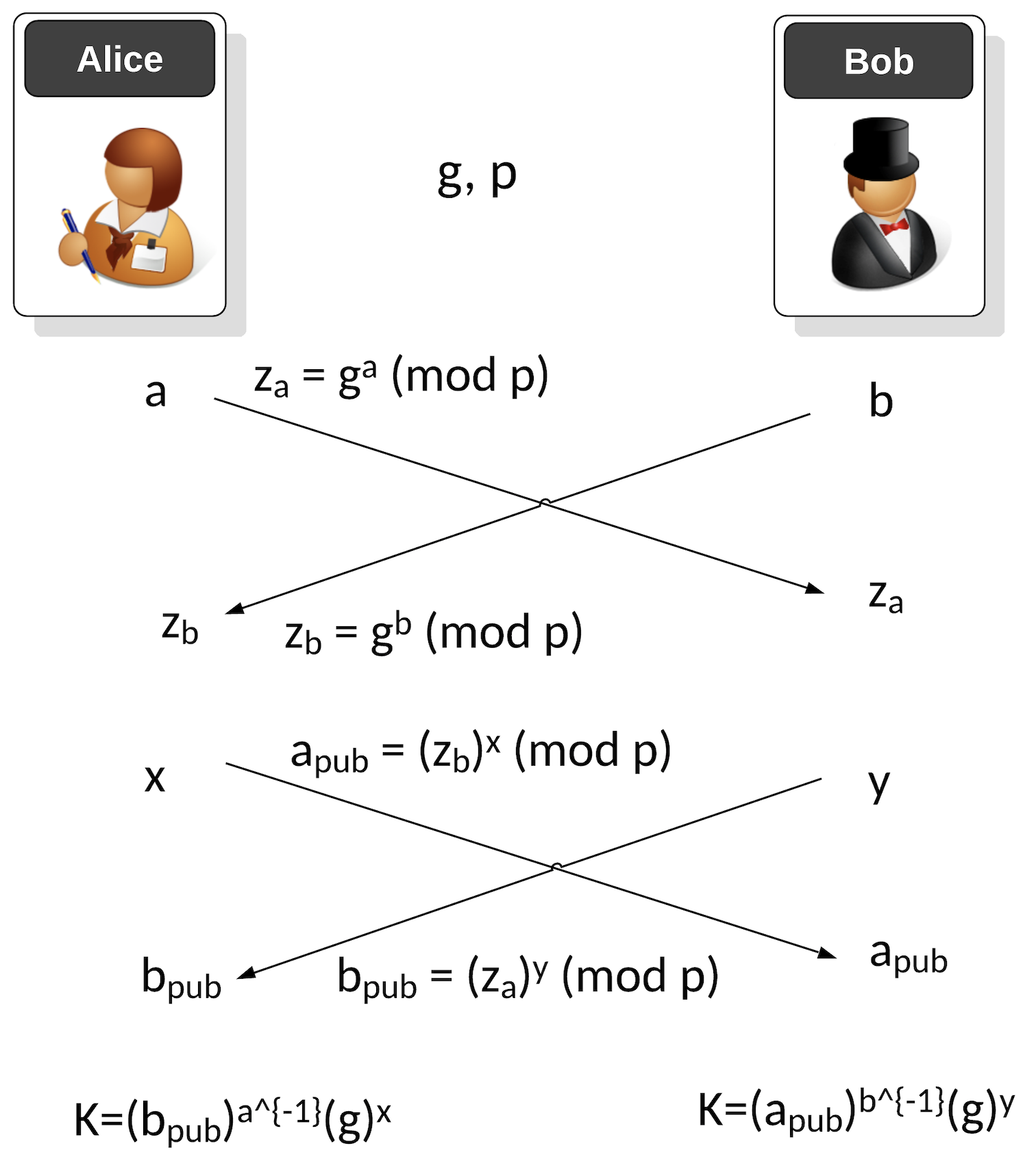
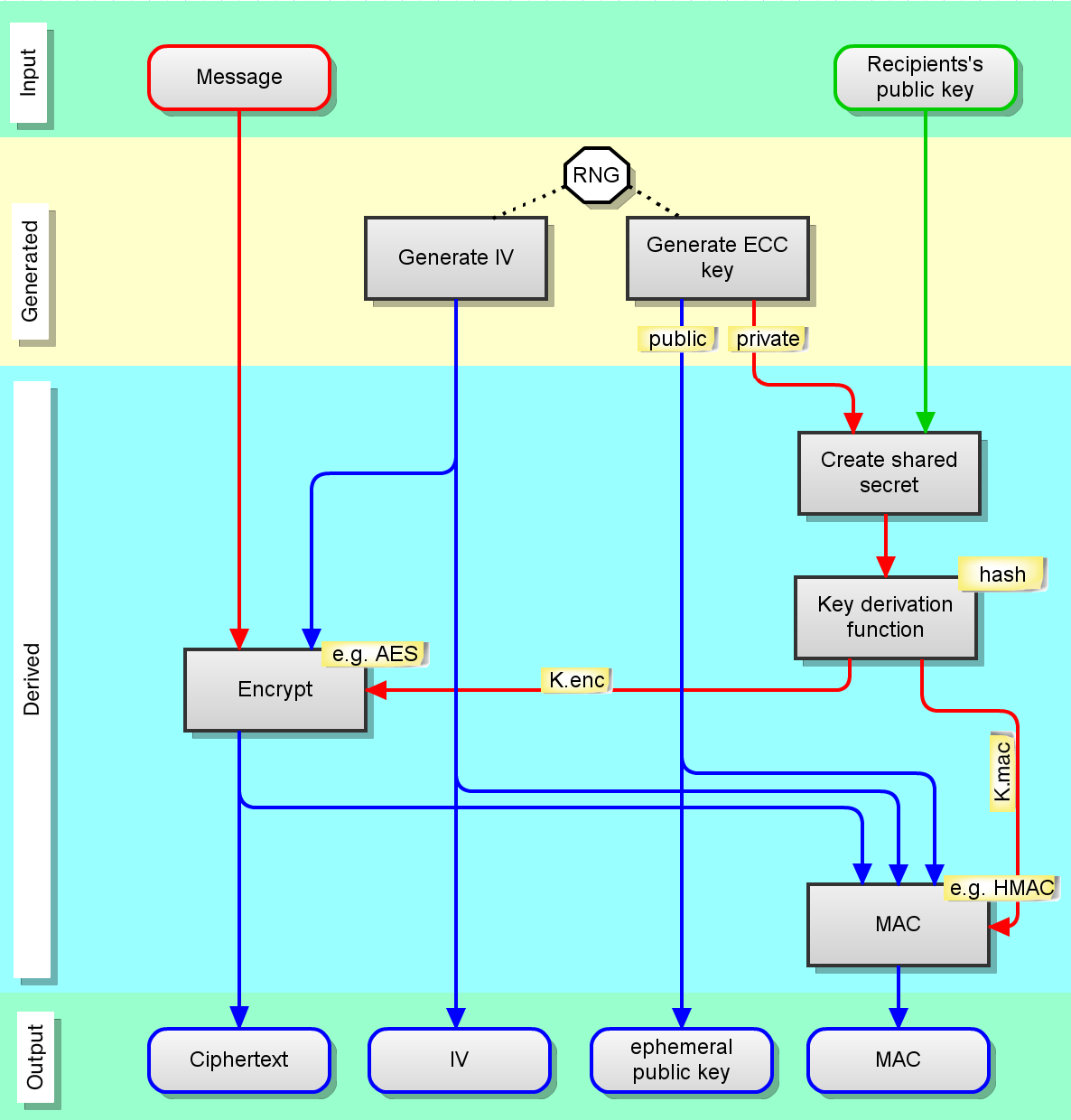
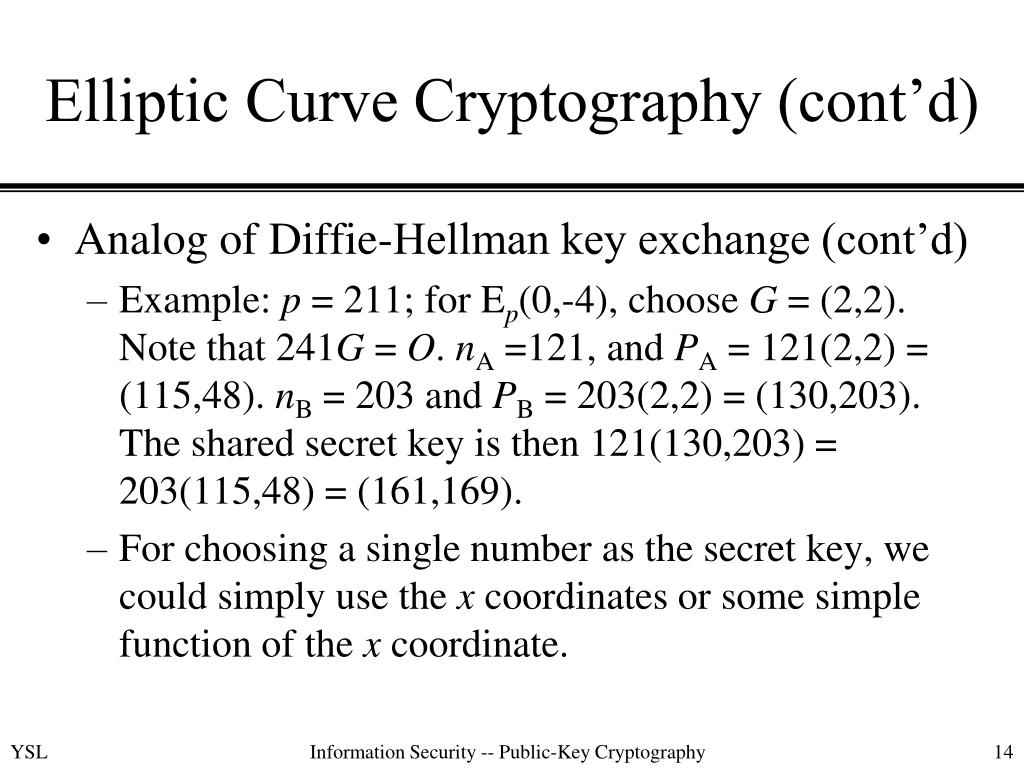
Elliptic Curve Diffie-Hellman (ECDH) Key Exchange Protocol. Two users,... | Download Scientific Diagram

The Security Buddy on X: "How does Elliptic Curve Cryptography work? https://t.co/f6k3Mbb0ls #security #encryption #ECDH https://t.co/z6uYu73g32" / X